-

Deception Technology 101 – from a Deception Engineer
•
we are not only engineering technical solutions to serve as decoys, canaries, etc, we are also engineering environments and, most importantly, we are storytellers.
-
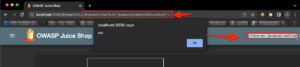
Finding security bugs across a codebase for beginners
•
A while back I was interviewing for a security role at a rather large company annd a big focus was finding bugs across different projects. Without going into a ton of detail, it’s safe to say that I didn’t exactly land that job at the time. Coming from a pentest/red-teaming…
-

How I transitioned into security, and what I would do differently (2022 edition)
•
I was visiting my parents over the winter holiday back in 2018. The cold air nipped at my bare arms and the North East Coast breeze was a stark reminder of how much colder it gets versus the warmth of the West Coast; I was running outside to catch a…
-
Securing your CI: How to determine what matters most
•
Over the last few weeks, I’ve been working to inject security tooling into the CI (continuous integration) pipeline. Coming from a background that’s primarily red-teaming, offensive security, and even a bit of compliance, there have been some learning curves for adapting security tooling to fit your organization’s needs. Given I’m…
-

What the OSCP doesn’t prepare you for in the workforce, and how to get caught up!
•
When I took my OSCP exam, I had less than two years of professional experience in the security space. While I did some of my own learning in terms of webapp testing, hackthebox scenarios, and the PWK (Pentesting with Kali) material, it doesn’t replace working alongside your peers on a…
-

Docker Cache Poisoning – Part 1
•
Introduction Docker is amazing – period. Having used Docker in personal and professional settings has been incredibly useful. The big idea here is that if an application can be “containerized” using Docker, it can run anywhere the Docker engine is installed. Most importantly, and interestingly, Docker containers can be configured…
-
Homoglyphs and Bypassing Web Application Controls
•
As with most articles I write, this post comes from a particular engagement where I was tasked with re-testing fixes engineers put in place for a XSS (Cross-Site Scripting) vulnerability. While the details of the exploit will not be discussed here, the bypass technique using homoglyphs are fair game. What’s…
-
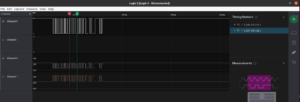
Unique – Retired HackTheBox Hardware Challenge
•
I’ve been staring at the Hardware section of HackTheBox for a long time now. Having had a past career in the automotive world myself, I finally decided to give Unique a go. The goal here is to find the VIN of the car that is repeated over and over again.…