I’ve been staring at the Hardware section of HackTheBox for a long time now. Having had a past career in the automotive world myself, I finally decided to give Unique a go.
The goal here is to find the VIN of the car that is repeated over and over again.
Here’s what you’ll learn:
- Serial/CAN Analysis with Logic2
- Some command line tricks for manipulating data
Discovery
When you download the ZIP file from hackthebox and extract it, you’re immediately greeted with one file – trace_captured.sal.file.
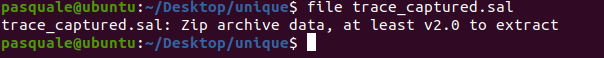
In this case, the .sal file is actually Zip-compressed data and can be extracted like a normal Zip archive with Unzip. Unzipping the files leaves us with a few digital and analog binary files along with a meta.json.
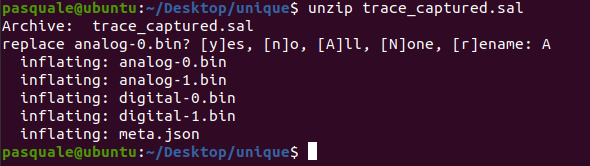
You can try to run the files through hexdump and strings, but the information might not be super interesting. However, viewing the header of the file gives us a clue:
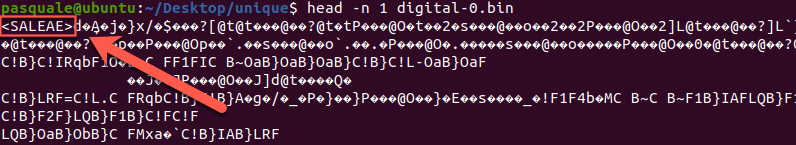
SALEAE is a company that creates debugging hardware and software. For the uninitiated, Saleae creates components that allow users to debug hardware by attacking probes to a device and analyzing the binary output transmitted. I’m no expert, but it sounds like someone did some hardware hacking on our target car. This means Saleae also has a debugging tool for Windows, Mac, and Linux. Proprietary software for proprietary file types? Let’s give it a go.
Once installed, the original trace_captured.sal file can be opened. Now, let’s analyze.
Analyzing the .sal file
Logic2 comes with an “Analyzer” function which, I assume, contains different kinds of preset analysis options for reading raw protocols. For our use, since this is an automobile, we’ll want to use CAN.
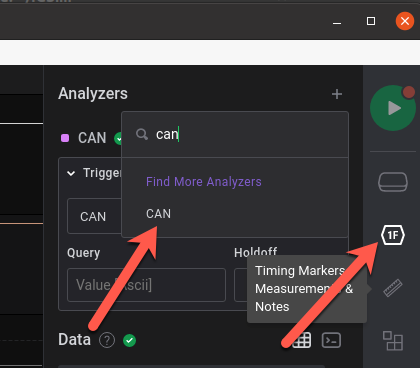
As an aside, Yogesh Ojha has a wonderful articles on car hacking 101 which cover the CAN protocol in more detail.
https://medium.com/@yogeshojha/car-hacking-101-practical-guide-to-exploiting-can-bus-using-instrument-cluster-simulator-part-i-cd88d3eb4a53
You’ll see below that after choosing a few different transfer rates between 120,000 and 130,000, we start to see some characters.
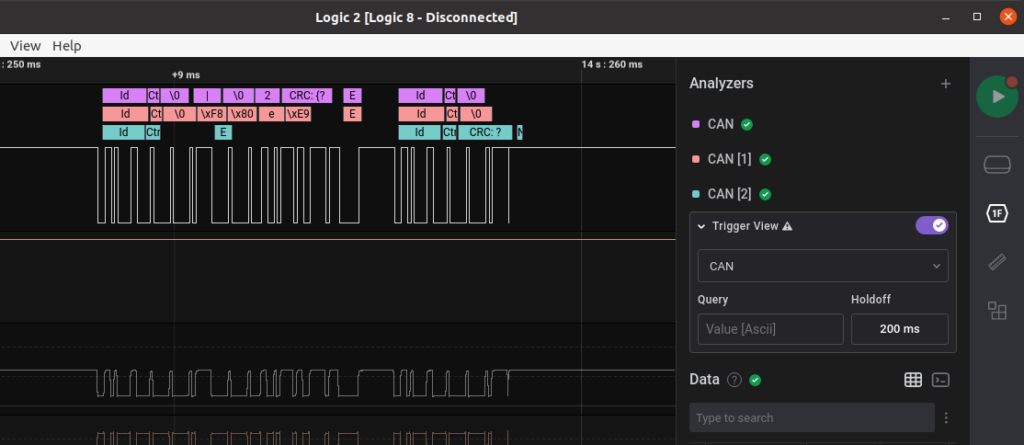
One thing that’s interesting is that we see a string of characters that contain CRC:{? which suspiciously looks like the syntax of a HTB flag. This Analyzer was used with the 125kb/s rate.
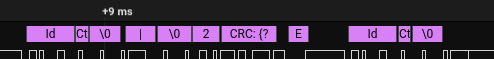
Logic2 lets you search in the data field and after coming across a few { characters, I start to see something that makes sense.
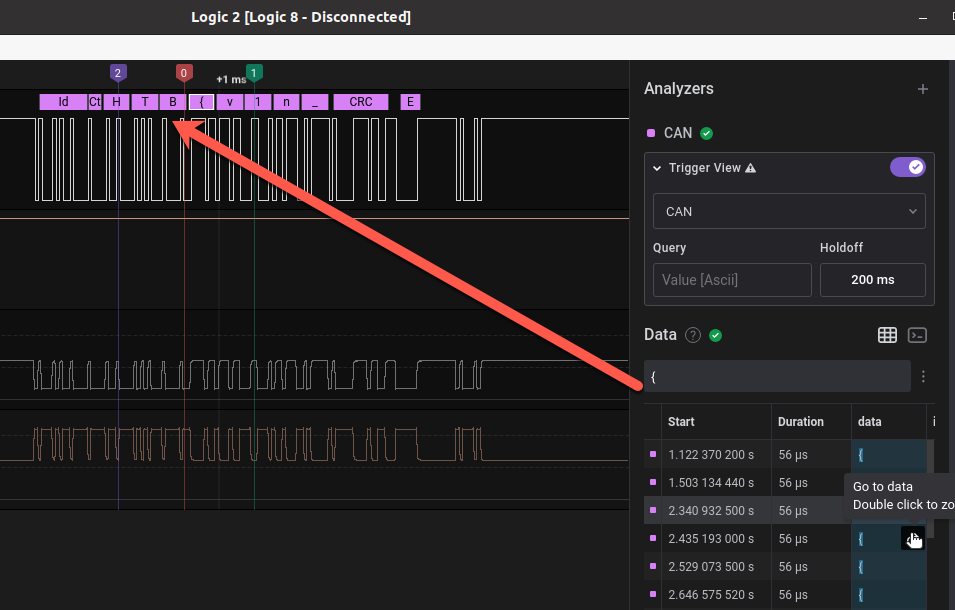
Now, export the table to a csv file.
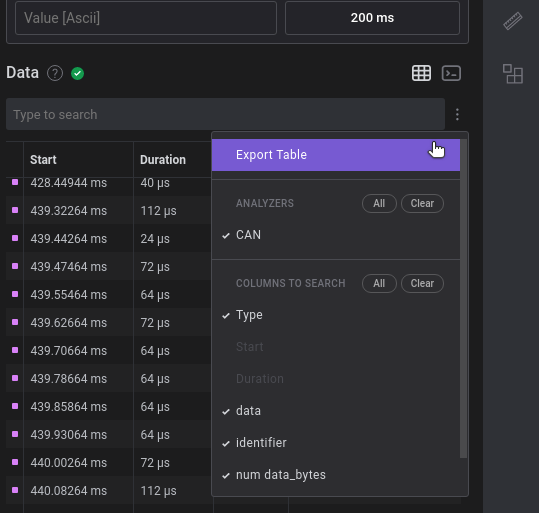
Further glancing at the CSV file, you can now see that the HTB characters are standing out. It’s just a matter of time before they’re extracted.
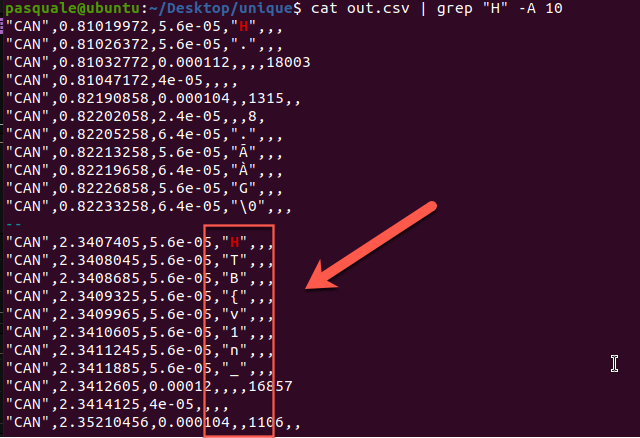
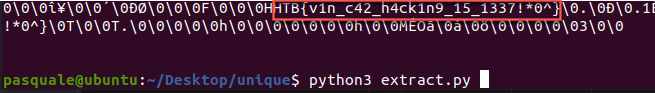
There are going to be tons of ways for you to extract the flag now that you know where things are heading. For me, a quick and dirty python script was enough for this task even if the output wasn’t pretty.
import csv
file = open("out.csv", 'r')
reader = csv.DictReader(file)
flag_string = ''
join_flag = False
for line in reader:
data = line['data']
print(data)
if data != '':
if data == 'H':
join_flag = True
flag_string += data
if join_flag:
flag_string += data
print(flag_string)
else:
passThe output? Messy, but works!